Prerequisites
The method shown in this article is implemented on a Ubuntu 24.04. server with the uncomplicated firewall (UFW) frontend for iptables enabled and configured. You also need a domain for which you can update the A (or AAA) record to point to the IP address you want to install in your firewall rules as a generall “allow” rule. In my case, I have a special subdomain called lifeline.baltic-lab.com. I am already curious how many requests I’ll see in my DNS logs for that subdomain after posting this article… 🙂
Bash Script
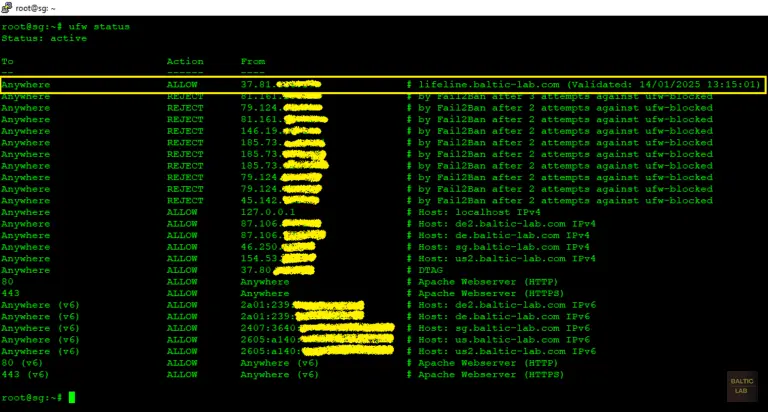
The script makes a DNS requests to the domain provided and retrieves the corresponding A record. If the script is running on this subdomain for the first time, it’ll install this IP address in the firewall rules using the “ufw prepend allow from” command. The “prepend” part ensures that the rule is put at the top of the list. This is particularly useful because UFW executes the first rule it finds on a match first. In case you locked yourself out through some dynamic system, Fail2Ban for example, this new rule will take precedence over the block rule. The installed IP address will be logged to a text file named “example.com.log” located in /var/log/. If the logfile already exists, the script will compare the IP address retrieved from the DNS record with the already installed rule. If they match, the comment is updated to the current time. That way the functionality can easily be verified by viewing the current firewall rules, for instance by executing the command “ufw status”. In case the IP has changed, the new IP will be installed and the old rule will be removed.
#!/bin/bash
HOSTNAME=lifeline.example.com
LOGFILE=/var/log/$HOSTNAME.log
Time=$(date '+%d/%m/%Y %H:%M:%S');
Current_IP=$(host $HOSTNAME | tail -n1 | cut -f4 -d ' ')
if [ $LOGFILE = "" ] ; then
ufw prepend allow from $Current_IP comment 'lifeline.example.com'
echo $Current_IP > $LOGFILE
else
Old_IP=$(cat $LOGFILE)
if [ "$Current_IP" = "$Old_IP" ] ; then
ufw allow from $Current_IP comment "lifeline.example.com (Validated: $Time)"
else
ufw delete allow from $Old_IP
ufw prepend allow from $Current_IP comment 'lifeline.example.com'
echo $Current_IP > $LOGFILE
echo Firewall rules for $HOSTNAME have been updated
fi
fiThe script can be executed automatically through an entry in your crontab. Make sure that the user for the crontab has sufficient privileges to update the firewall rules. If everything is installed correctly, the firewal rules will be updated through cron in the time interval defined in the crontab. Whether this is used to install a “backdoor” as a lifeline through the use of a manually updated DNS record, or to dynamically allow full server access only from an IP address in a DynDNS record is up to you.
Westerhold, S. (2025), "Firewall Rules with (dynamic) DNS Hostname". Baltic Lab High Frequency Projects Blog. ISSN (Online): 2751-8140., https://baltic-lab.com/2025/01/ufw-iptables-firewall-with-dynamic-dns/, (accessed: January 16, 2026).
- Conducted Emissions on the Bench: Implementing the CISPR 25 Voltage Method - December 15, 2025
- WebP-Images without Plugin - January 14, 2025
- Firewall Rules with (dynamic) DNS Hostname - January 14, 2025